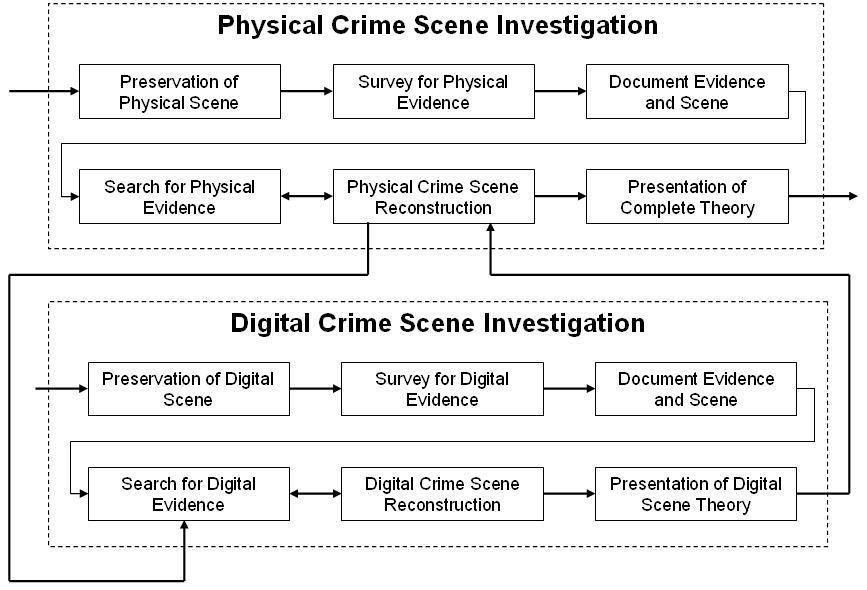
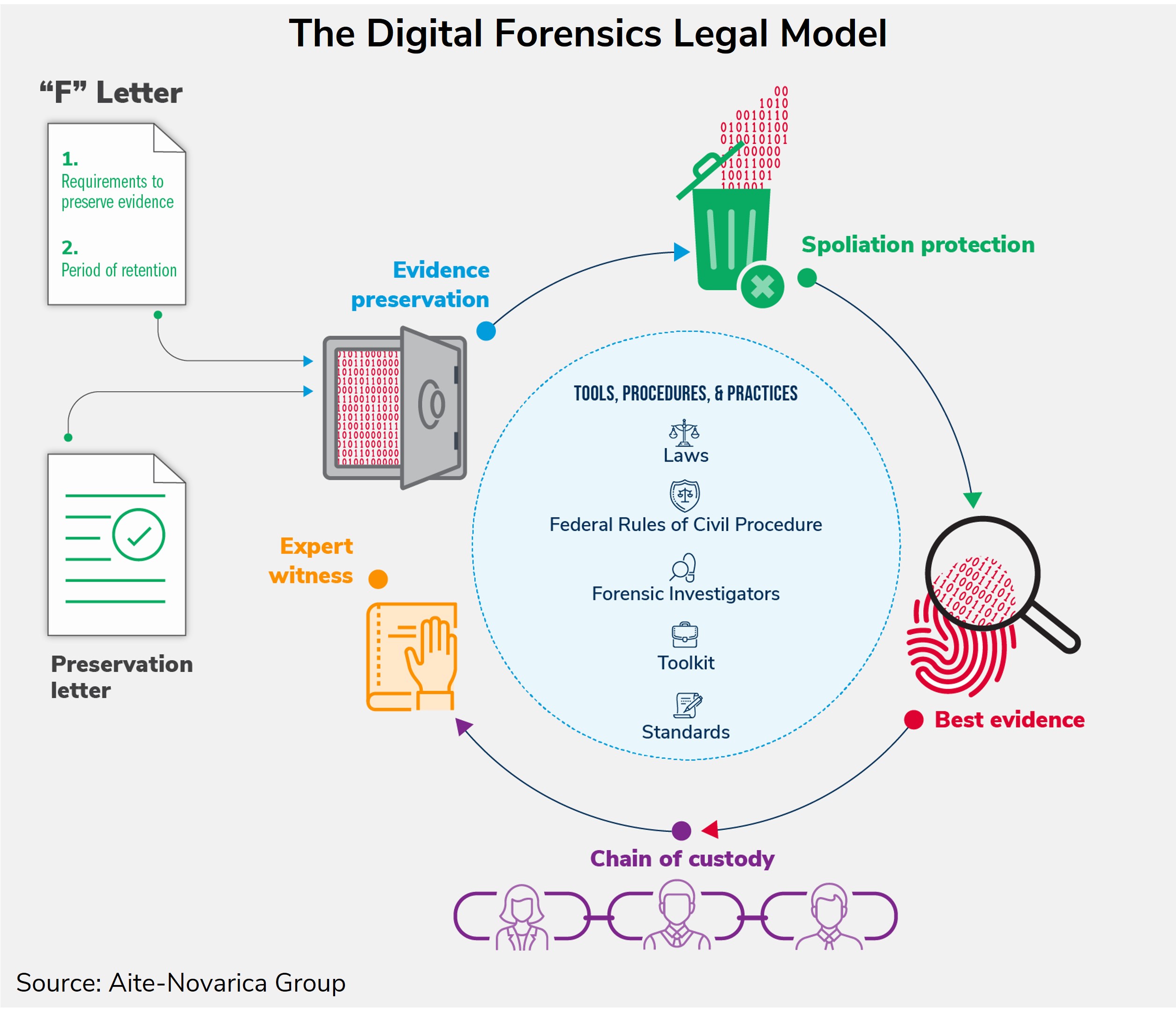
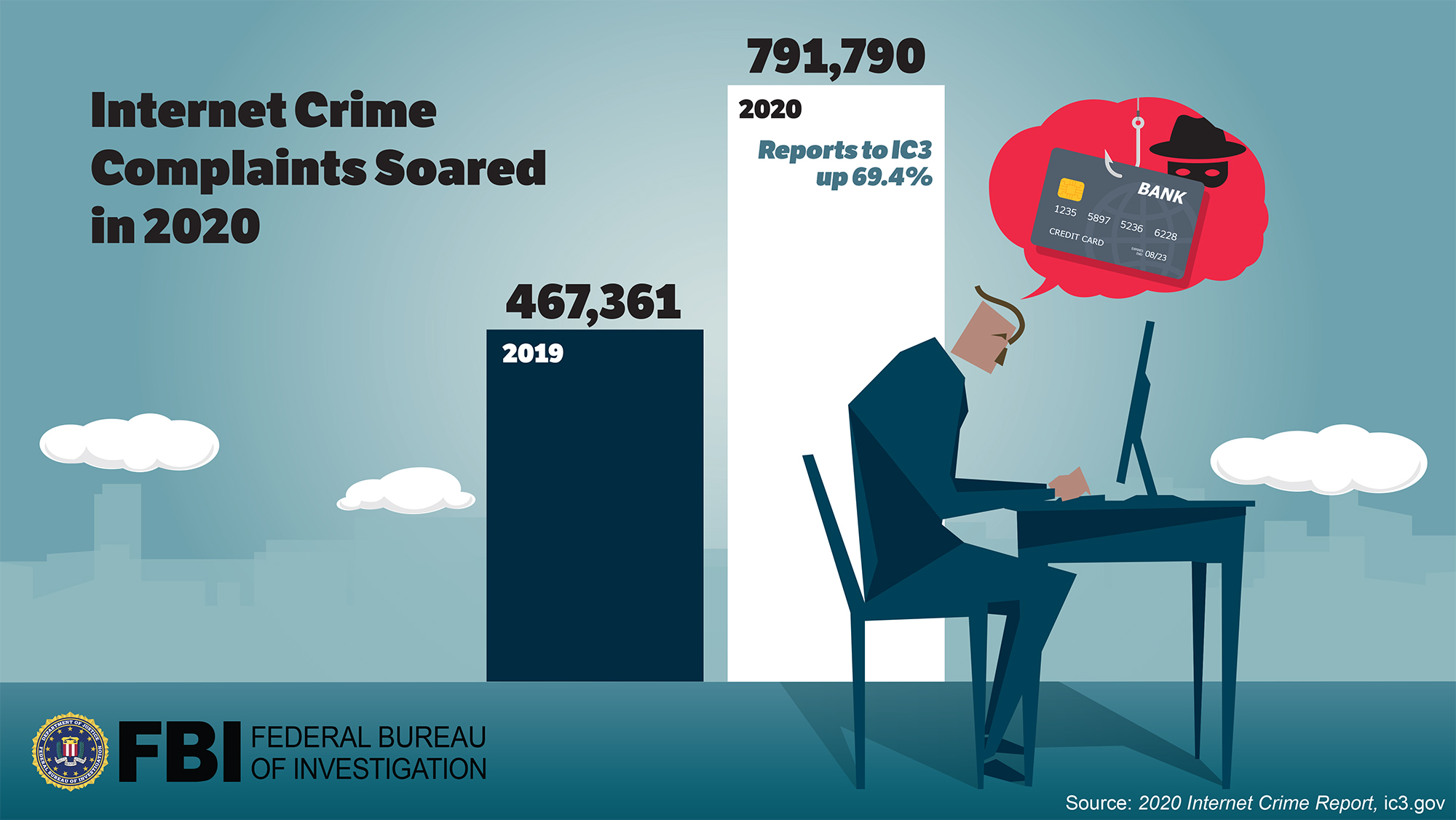
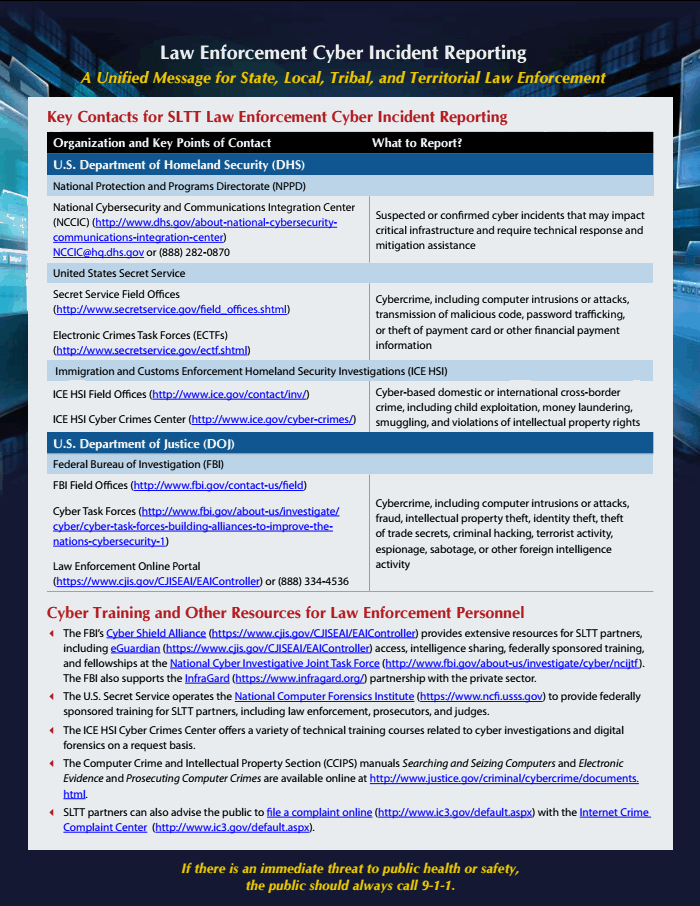
Identifying Law Enforcement Needs for Conducting Criminal Investigations Involving Evidence on the Dark Web | RAND

Cyber attack. Law enforcement. Criminal stealing money online. Computer forensics, digital forensic science, computer crime investigation concept. Bright vibrant violet vector isolated illustration Stock Vector | Adobe Stock

Amazon.com: Computer Crime, Investigation, and the Law eBook : Easttom, Chuck, Taylor, Jeff: Kindle Store

Cyber attack. Law enforcement. Criminal stealing money online. Computer forensics, digital forensic science, computer crime investigation concept. Pin Stock Vector Image & Art - Alamy

9781305507333: Computer Crime, Investigation, and the Law - Easttom, Chuck; Taylor, Jeff: 1305507339 - AbeBooks